SCIM
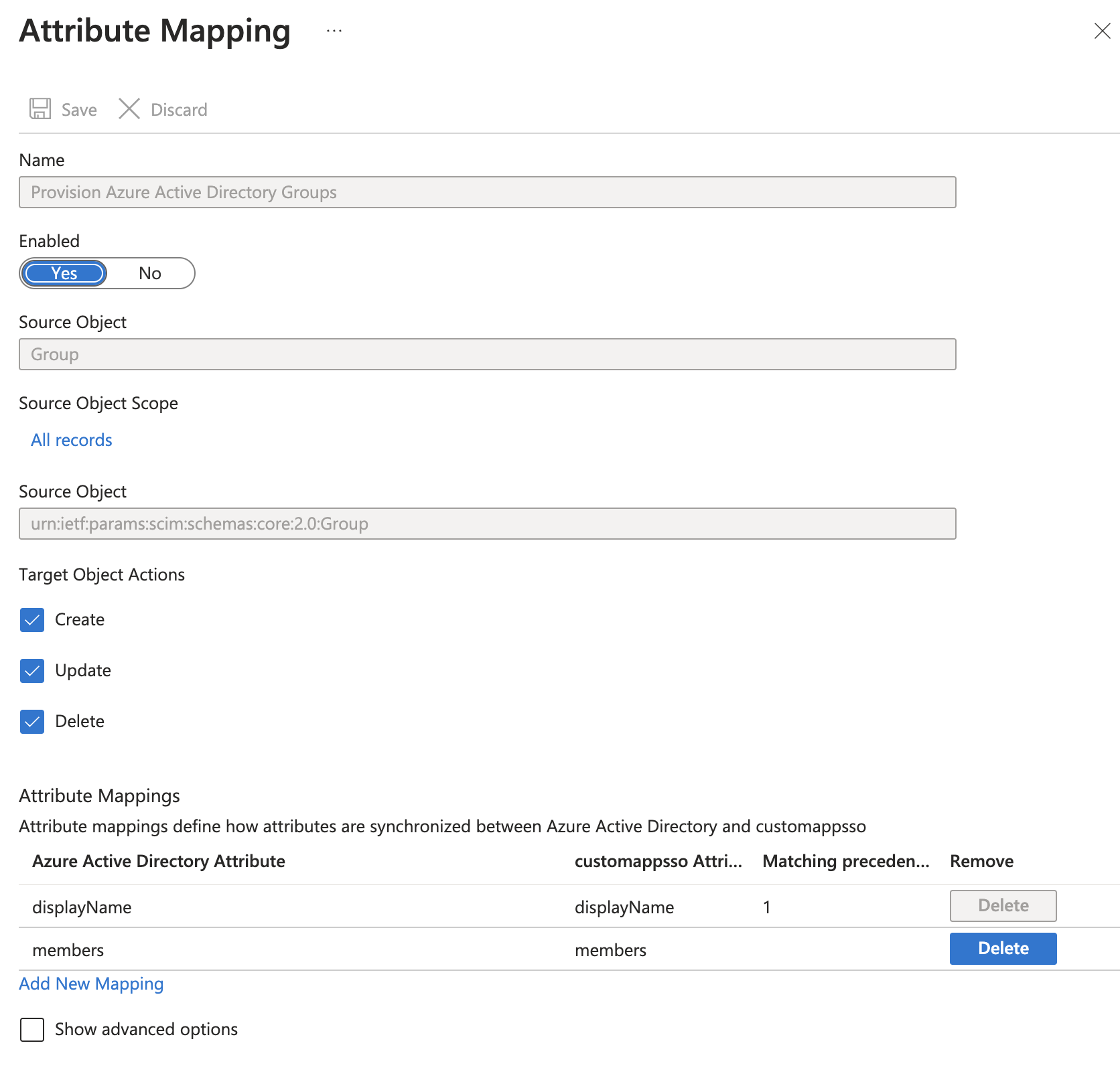
In order to provision user to the new ODJ users service the ODJ will provide a SCIM interface. This interface is then used by our Cloud-IDP (Azure Active Directory (AAD)) to provision users to the ODJ.
There will is an AAD group and all users that are part of that group will be synced into ODJ.
Unfortunately, there is a speciality in AAD, only a small set of TLS certificate authorities are supported for the SCIM service. None of the CAs used at Schwarz IT can be used. Therefore, we implement a SCIM proxy service that we deploy as a consumption-based Azure Function. It acts as a "dumb proxy" and forwards all requests from the AAD to our SCIM service. Through this workaround, we automatically receive a valid certificate for the Function from Azure which is also accepted by the AAD.
The SCIM service adapts the information received via SCIM and performs user additions/changes or deletions via the interfaces of the user service.
Provisioning interval
Provisioning happens on a fixed interval of 40 minutes which is configured by the administrators of the tenant. This means that changes to users or permission changes can take up to 40 minutes to get through to ODJ.
SCIM standards compliant behavior
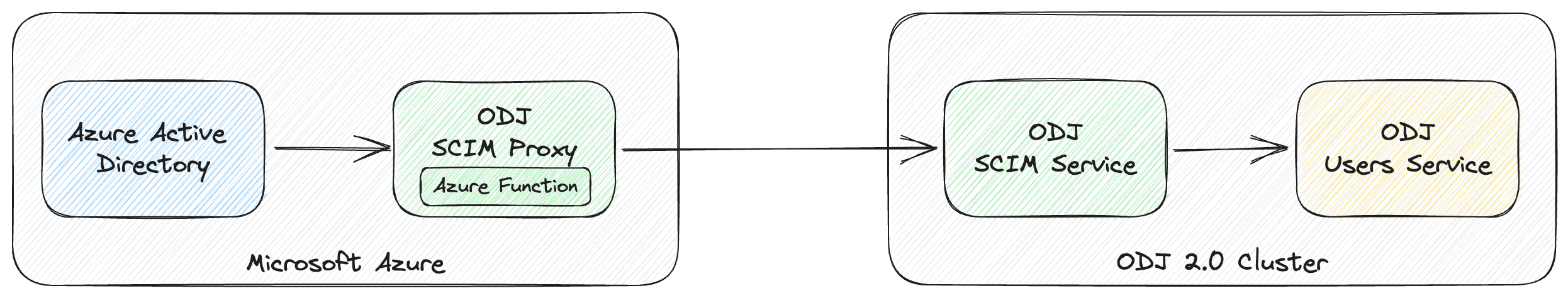
The default SCIM implementation of Azure AD is not standards compliant. In our case, this mainly concerns the active attribute. In Azure AD this attribute is treated as a string, but in standard it is a boolean. To get this behavior in Azure AD a feature flag must be enabled in AAD.
To activate the standards compliant active flag, an ?aadOptscim062020 must be appended to the SCIM URL.
Groups endpoint
To support the provisioning of an Azure AD group, the group endpoint must be implemented, even if it is only a single group. Otherwise, no users will be synchronized as long as the configuration is designed for group memberships.
Since we are not interested in the details of a group and all synchronized members are members of this one group anyway, we do not need to persist the group data.
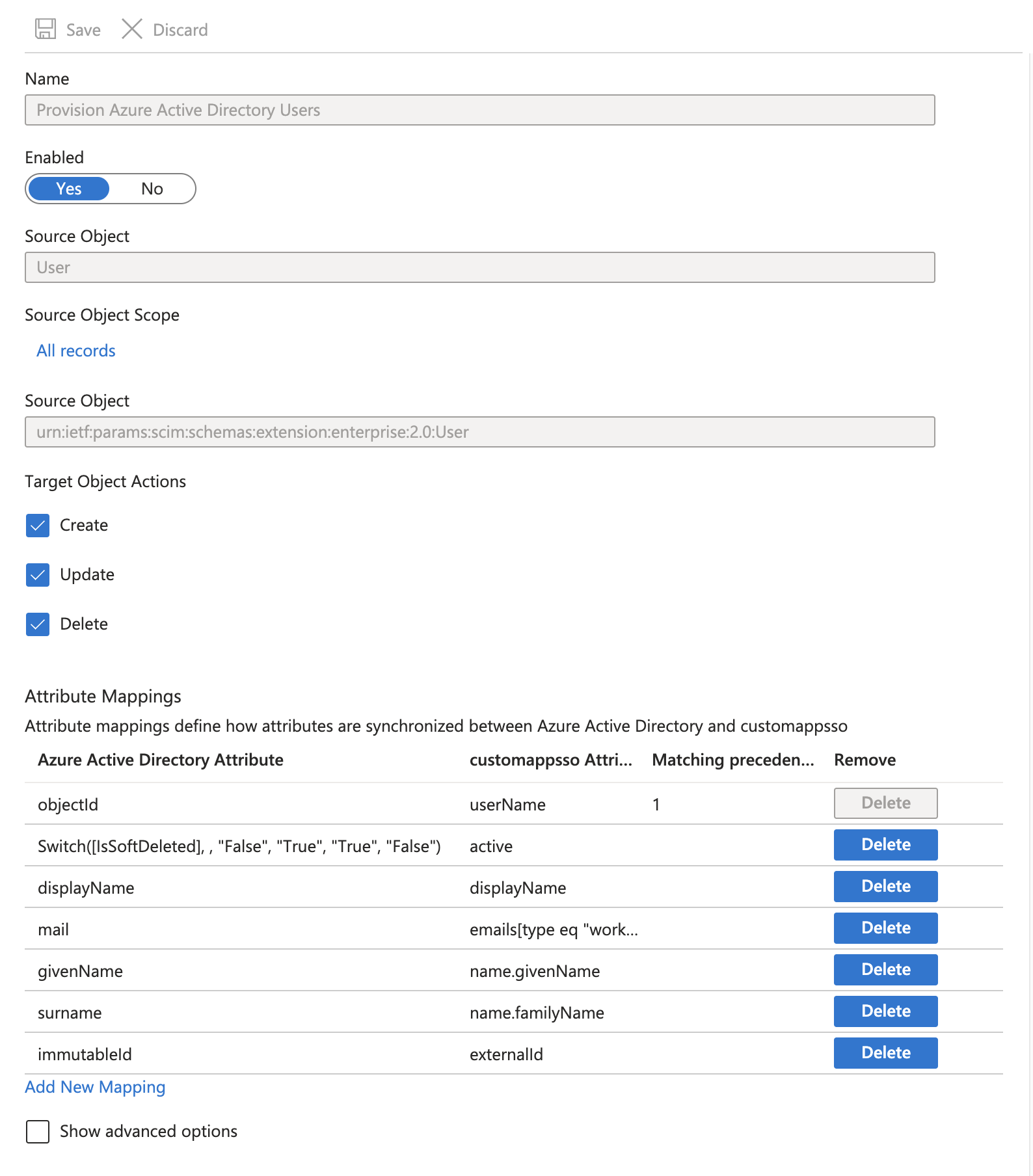
Users Mappings
To support our user schema, the following mapping settings must be made in Azure AD:
Groups Mappings
To support our fake groups schema, the following mapping settings must be made in Azure AD: